How to trust applications downloaded online
Today, almost all the applications on your computer are downloaded from the Internet. This gives cybercriminals a chance to obtain the source code of an executable file, for instance, insert malware into it, and allow the program to be found and downloaded online. Any user downloading and installing this file would fall victim to the malware.
To prevent this, your operating system does not allow the installation to proceed without checking for the existence of a code signing certificate. In the case of a missing certificate from a recognized vendor, the user is alerted to this, and can then choose to proceed with the installation or not.
However, users often do not delve into the messages displayed with sufficient severity and may damage the data on their computer with infected software.
Validating Susan.one application
Most consumer operating systems are pre-configured to check for the presence of a code-signing certificate before an application is installed. When an installation is prompted, the OS first confirms the legitimacy of the certificate and when the certificate does not exist or it's not issued by the recognized vendor, OS informs you that the application is not from a trusted source.
In fact, you can verify the validity of the software quite easily before you install it. On Windows OS make right-click on the executable file and choose "Properties" from the menu.
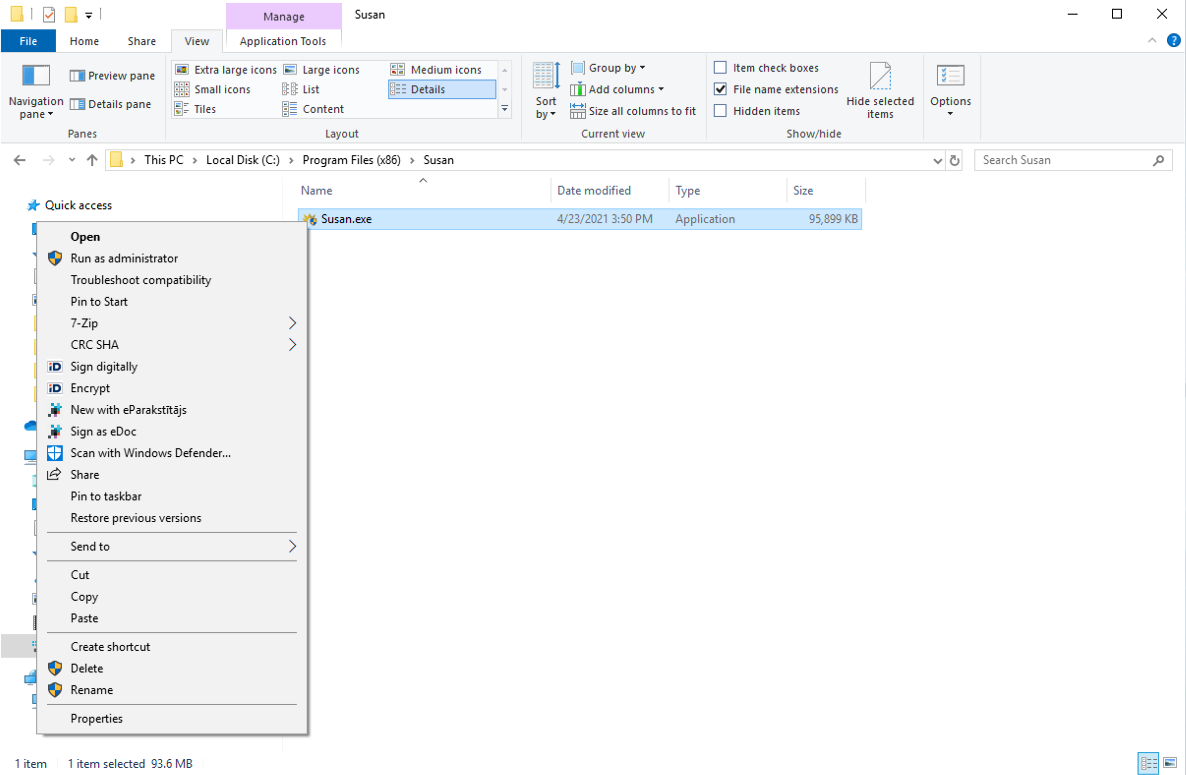
In the properties window, navigate to the "Digital Signatures" tab and from there you can see the list of the signatures. In Susan.one case, there must be signature signed by Susan.one Ventures.
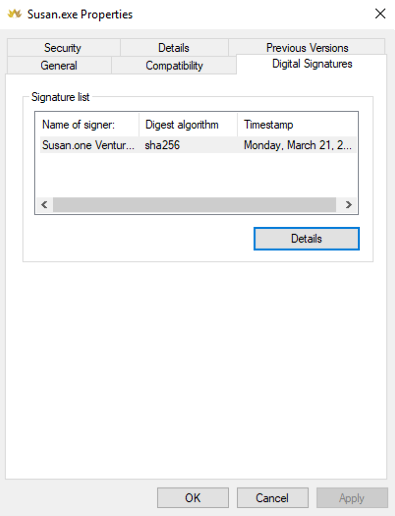
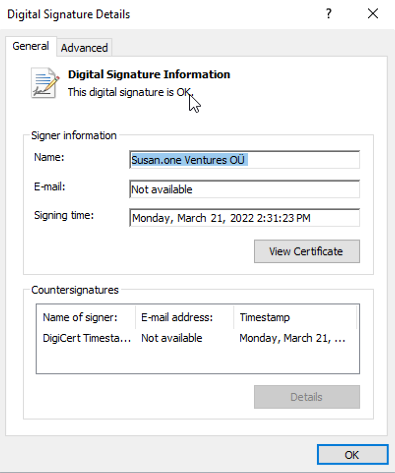
Click on the "Details" button to investigate signature information. This window will display signer information and reports, is signature ok or not.
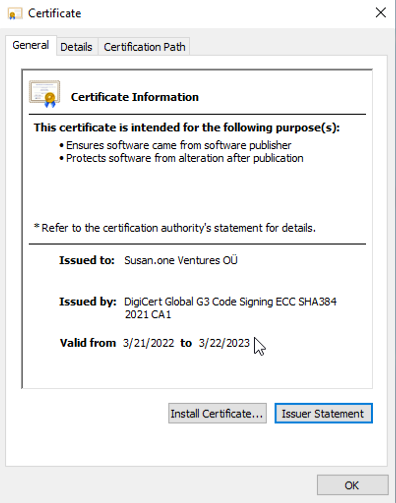
Now you can look certificate information by clicking to "View Certificate" button. If you see the same information as in the image below, you can be sure that the application was released by Susan.one and has not been altered in any way since the release.
Summary
There is inevitably a risk associated with software downloaded from the Internet if you cannot be sure that the software is from the manufacturer and has not been modified by third parties. This method described in this article will help you identify the source of each software and reduce the potential damage to your computer.
However, it doesn’t mean that digitally signed software is one hundred percent bulletproof. There have been cases, where malware implanted in signed software too by stealing the certificates or private keys. But these are rather rare cases, as manufacturers protect their private keys and certificates very carefully, as do we.



Comments
Post a Comment